I ran into 2 issues while using the vCenter Server Appliance and integrating it with AD and what I found I figured might help some of you in the future. Here goes:
Issue 1: vCSA fails to join the AD domain.
On the initial deployment of my vCSA I got an error while attempting to join my AD Domain that says “Error: Enabling Active Directory failed”. That’s it… nothing useful…
When this happens you can run the process manually and if it fails you will at least get an error code. To do so run /usr/sbin/vpxd_servicecfg with the following syntax:
vpxd_servicecfg ad write <username> <password in 'single’ quotes> <domain name>
like:
vpxd_servicecfg ad write caleb ‘myTopSecretPa$$’ caleb.com
If it is successful the return code will be “VC_CFG_RESULT=0”. If that is the case you need to reboot your vCSA and you are ready to roll.
Issue 2: Configuring vCSA to use AD for user authentication with LDAPS.
1: Login to the web client (NGC) on your vCSA (https://<vCSA>:9443/vsphere-client.)
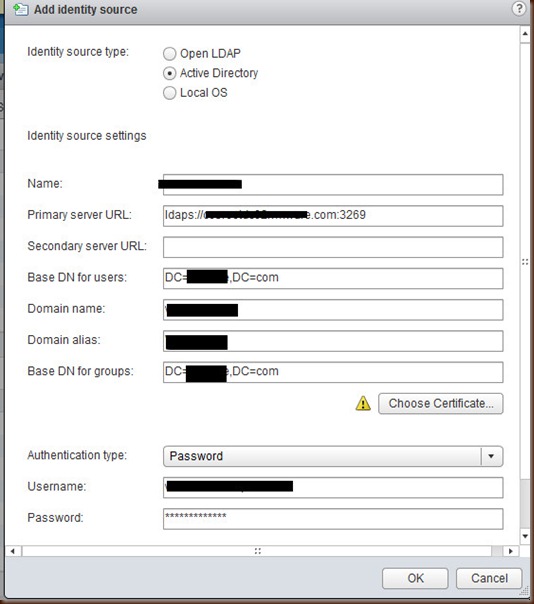
2. Go to Administration > Sign-On and Discovery > Configuration and click on the little green plus to add an identity source. Now you should see a screen like the below:
For the most part it is all pretty simple, the gotcha is the primary server URL and the “Choose Certificate” button. For additional useful information look at the vmware documentation at http://pubs.vmware.com/vsphere-51/index.jsp?topic=%2Fcom.vmware.vsphere.security.doc%2FGUID-B23B1360-8838-4FF2-B074-71643C4CB040.html.
Next I need to get a certificate so I can talk to the DC. This part is pretty easy once you think about it for a minute. From my Windows workstation I open up MMC and add a Certificates snap-in for the Local Computer account. Next expand you certificates and navigate to the “Trusted Root Certification Authorities” folder and find the certificate that was issued by your Domain’s Certificate Authority. That is the certificate that we will use.
Right click on the proper certificate and go to All Tasks > Export. Change the format to Base-64 encoded X.509 .cer and save to your local desktop. Next from the vCSA “Add Identity Source” window click on the “Choose Certificate” and point it at the cert you just exported. Congratulations your domain logins will now work, just don’t forget you still need to assign them permissions.

OK so I am getting the same "Error: enabling Active Directory failed." Running the script on the box give error #302 which is "ERROR_AD_ENABLED_FILED=302." What did you do to resolve this?
ReplyDeleteI'm getting the same "302" error, but so far have not found a fix.
ReplyDeleteGo to the Network tab and then Address. The hostname for your server needs to be on the domain you are joining. I believe the default is localhost.localdomain. If your domain is domain.local you need to change the hostname to vcenter.domain.local. Then add the domain.local AD settings to the authentication tab. Hope that helps.
ReplyDelete